Securing information has become complex. With advanced technology and modified threats, the efficiency of cryptography is greater than ever. It is the practice of protecting sensitive information through coded algorithms, hashes, and signatures. Online transactions, password protection, email encryption, and safeguarding essential domains require strong and efficient methods. One of the most widely used methods for secure encryption is the Cipher Feedback Mode, commonly known as CFB Mode.
CFB Mode is ubiquitous in modern-day systems. Coding is a necessary skill required in this digitalized outlook of the world. If you’re interested in encryption, development, data security for worldly organizations, or geek-inspired spy movies, understanding the advantages and disadvantages of CFB Mode is essential.
In this blog, we’ll decrypt what CFB is, how it works, the mathematical formula, and the major pros and cons.
✦ What is Cipher Feedback (CFB) Mode?
CFB (Cipher Feedback) Mode is one of the operational modes used with block ciphers like AES (Advanced Encryption Standard). It was developed to allow block ciphers to work as stream ciphers. Instead of encrypting large blocks all at once, it processes small amounts of data, sometimes even bit-by-bit, making it well-suited for systems where data arrives continuously or in real-time.
➣ In CFB Mode:
- A block cipher encrypts an initialization vector (IV).
- The output is XORed with the plaintext to produce the ciphertext.
- The ciphertext then becomes input for the next encryption cycle.
✦ How Does CFB Work?
So, how does CFB work? It is important to understand this before discussing the advantages and disadvantages of CFB mode.
Advantages and Disadvantages of CFB Mode works differently from ECB by making each encrypted block dependent on the key, which is the current plaintext block and the previous ciphertext block. The encryption adapts based on the message, making it more secure.
A unique trait of CFB is that it only uses the encryption part of the cipher, even during decryption. A distinctive trait of CFB is that it only uses the encryption part of the cipher, even during decryption. This distinguishes it from other modes because it doesn’t use the decryption function.
CFB turns a block cipher into a stream cipher. It creates a keystream using the encryption machine algorithm and then mixes that with the plaintext using XOR. This gives CFB the flexibility of a stream cipher while keeping the security of a block cipher.
However, one drawback is that an error in one block during transmission can affect the following few blocks since they’re all linked.
✦ The Algorithm
CFB mode uses an initialization vector (IV), the encryption function of the block cipher, and a segment size known as k.
1. Start with an IV (Initialization Vector): First, the system picks a random or pseudorandom IV. This IV must be the same length as the cipher’s block size.

2. Encrypt the IV: The IV is encrypted using the block cipher and a secret key. This creates an output block that will help generate the ciphertext.
3. Create the Keystream Segment: The system takes the first k bits (often 8 bits or 1 byte) from the encrypted IV. This portion is used as a temporary keystream to mask the plaintext.
4. XOR with Plaintext: The keystream is XORed (bit-by-bit mixed) with the next k-bit segment of plaintext. This creates the first piece of ciphertext.
5. Update the IV for the Next Round: The IV is shifted left by k bits. The leftmost k bits are discarded, and the newly created ciphertext segment is added. This updated IV becomes the input for the next round.
6. Repeat the Process: These steps continue for each plaintext segment until the entire message is encrypted.
✦ What are the advantages and disadvantages of CFB mode?
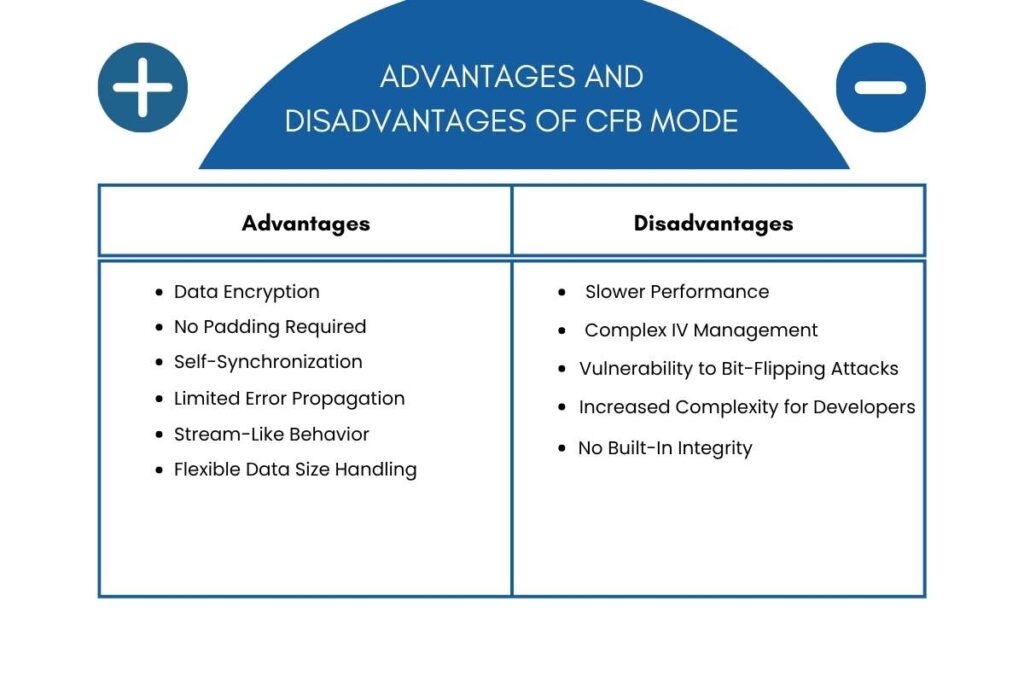
➣ The Upsides:
1. Data Encryption
CFB Mode is designed to encrypt data as it comes in. This makes it perfect for streaming services, voice communication, or any scenario where waiting to collect significant data blocks isn’t possible.
2. No Padding Required
Unlike other modes like CBC or ECB, CFB Mode does not require padding. It can handle data that doesn’t neatly fit into block sizes, making implementation easier and more efficient.
3. Self-Synchronization

Self-synchronization is yet another advantage of CFB mode. The decryption process can be recovered after a few blocks, even if a few bits of data are lost or corrupted in transmission.
If a few bits of data are lost or corrupted in transmission, the decryption process can recover after a few blocks.
4. Limited Error Propagation
If a single bit is altered during transmission, only a small portion of the decrypted data will be affected. This is useful for systems prone to occasional data corruption, such as wireless communication.
5. Stream-Like Behavior
CFB converts block ciphers into stream ciphers. This hybrid behavior allows it to work with existing block cipher algorithms like AES or DES while also handling data in a stream-like manner.
6. Flexible Data Size Handling
It can be used effectively with data of varying lengths as it doesn’t rely on fixed-size blocks. This is helpful in interactive systems and network protocols.
➣ The Downsides:
Despite the strengths listed above, a complete understanding of the advantages and disadvantages of CFB Mode requires dissecting its weaknesses, too.
1. Slower Performance
CFB Mode works serially; each block must wait for the previous one to finish. This lack of parallelism can result in slower performance than other modes like CTR (Counter Mode).
2. Complex IV Management
Proper management of the Initialization Vector is critical. If the IV is reused or predictable, it can compromise the entire encryption process. Developers must implement strong IV policies.
3. Vulnerability to Bit-Flipping Attacks

CFB Mode does not offer any built-in message authentication. If an attacker modifies the ciphertext, they can cause predictable changes in the plaintext. This makes integrity checks a necessity.
4. No Built-In Integrity
CFB Mode ensures confidentiality but not integrity. That means you can’t be sure your data hasn’t been tampered with unless you implement an additional integrity verification mechanism like HMAC.
5. Increased Complexity for Developers
Although CFB doesn’t require padding, its use of feedback and IVs can make coding and debugging more complex for inexperienced developers.
✦ What are the standard encryption modes?
- ECB (Electronic Code Book) Mode
- Padding
- CBC (Cipher Block Chaining) Mode
- OFB (Output Feedback) Mode
- CTR (Counter) Mode
Conclusion
CFB (Cipher Feedback) mode significantly contributes to the block cipher modes of operation with its real-time encryption and flexibility. Although advantages and disadvantages of CFB Mode isn’t as widely used in modern systems as CTR, its distinct features still make it suitable for some older systems or specific cases where controlling error spread is essential. However, it does come with inevitable setbacks, like performance limitations and a lack of built-in integrity checks. Developers and data security professionals must understand the advantages and disadvantages of CFB mode to execute it accurately.
✦ FAQs:
Q1. Is CFB Mode better than CBC Mode?
A. CFB Mode is better for real-time and streaming encryption because it doesn’t require padding. CBC Mode is generally better for bulk encryption when speed and block alignment are essential.
Q2. Can CFB Mode be used without padding?
A. one of the benefits of CFB Mode is that it doesn’t require any padding, even when handling data of irregular length.
Q3. Does CFB Mode ensure data integrity?
A. No, CFB Mode provides confidentiality but not integrity. Additional mechanisms like HMAC are needed to ensure data is not tampered with.


















